SELinux is one of the most powerful security features in your Fedora system. It’s like a valet key for your computer services, only allowing them to access approved data. SELinux has outgrown its early-days reputation for difficulty. Now it has tunable policy for most popular applications, and provides extra security and confidence. However, sometimes errors do occur, and this article will help you deal with them.
Assumptions
This article assumes two things:
- You know the basics of SELinux. If you haven’t learned basics of SELinux, now is a great time to do that. One of the best primers is this video by Thomas Cameron. Take the time to watch and understand it.
- You’re using SELinux in enforcing mode. The enforcing mode is the normal and expected way to run Fedora. If you’ve disabled SELinux, you’ll need to enable it. Edit the /etc/sysconfig/selinux file to set SELINUX=permissive. Using permissive mode first ensures that any radical problems can still be fixed automatically by the following commands. Then do the following:
sudo fixfiles -F onboot reboot
The boot process may take longer than usual, since SELinux relabels any files created while it was disabled. This can take a while on very large file systems, so be patient.
Don’t be surprised if you start seeing errors after relabeling, if you’ve been running in disabled mode for a while. Running in disabled mode is like wallpapering over a leak. When you remove the wallpaper, you’re likely to find water damage. In the same way, if you’ve been running without SELinux enabled, you’ve probably created more problems that now need to be solved.
Once the machine has rebooted, you can switch to enforcing mode:
sudo setenforce 1
Is it really SELinux?
A good way to tell whether SELinux is at fault for an error is to set permissive mode. This means SELinux logs the error, but still allows the activity. To do this, run this command:
sudo setenforce 0
Then try the process again, in another terminal if needed. If it now succeeds, SELinux policy is fault. To find errors within the last 10 minutes, use the ausearch command:
sudo ausearch -m AVC,USER_AVC,SELINUX_ERR -ts recent
If the process still fails while in permissive mode, the problem is likely not the SELinux policy. In that case, make sure to run sudo setenforce 1 to return to enforcing mode. Remember this setting is global, so you don’t want to leave off policy enforcement everywhere!
Identify the problem
You can generally identify SELinux errors through the AVC message. One of the parameters of the AVC message is the command that generated the message. For example, you might see comm=”/usr/sbin/httpd” in a message about an SELinux error generated by the Apache web server.
The problem will also tell you the source context (scontext) of the acting part of your system, and the target context (tcontext) of the thing it tried to act on. Often, but not always, the source is a binary and the target a file. To understand the error better, you can use the SELinux Troubleshooter. You can install this from the Software tool in Fedora Workstation, or use sudo with dnf in a terminal:
sudo dnf install setroubleshoot
To start the program, use the Overview in Fedora Workstation to locate the SELinux Troubleshooter, or run from a terminal:
sealert
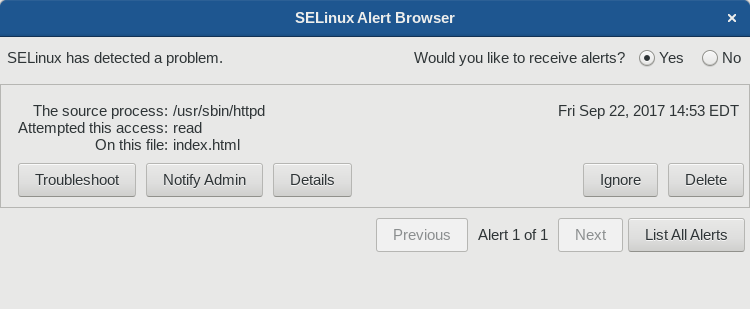
You can find recent alerts in the browser that appears:
At this screen, for example, you can list all the alerts present on your system to troubleshoot them systematically.
Fixing the problem
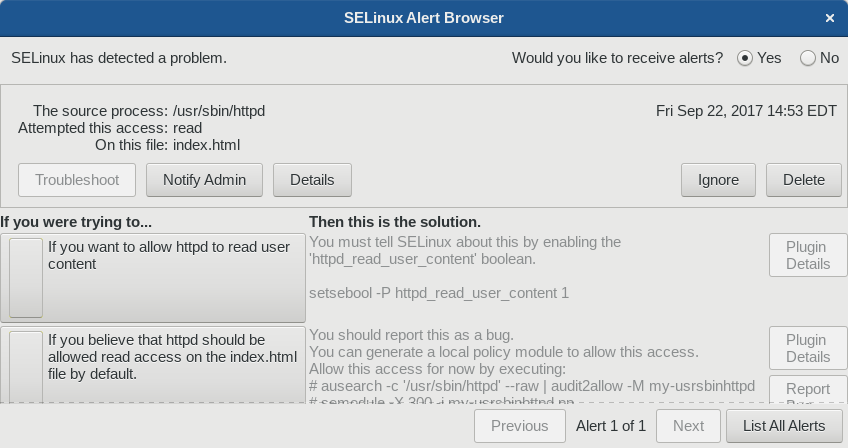
When you select Troubleshoot you’ll see several options for your error.
In this case, the user created an index.html file in their home directory, and used the mv command to put it in /var/www/html/ to be served by the Apache web server. After pointing a web browser at http://localhost/index.html, this error occurred.
Notice how each choice gives you a specific set of commands you can run to fix the problem. In this case, there is a boolean switch you can enable to allow the activity in the future, even while SELinux is enforcing policy.
However, just because a boolean exists doesn’t mean you should enable it without understanding it. In this case, if you turn on the boolean, the Apache web server will be able to read any user content whose file permissions allow it. So in this case, we might instead want to ask, “Why does the file have that context?” In this case it’s because the user moved the file. That means the file carried its old context into its new location, rather than receiving a new default context that allows the web server to read content in /var/www/html.
In this case, the best idea is to simply restore the file’s correct context:
sudo restorecon -rv /var/www/html/index.html Relabeled /var/www/html/index.html from unconfined_u:object_r:user_home_t:s0 to unconfined_u:object_r:httpd_sys_content_t:s0
A note about SELinux booleans
There are many booleans available. Each one allows you to set a broad class of access that may be expected for an application to function. To see the whole list and their current settings, run this command:
semanage boolean -l
If you install the selinux-policy-devel package first, you can also see a short description for each boolean when you run the command above:
SELinux boolean State Default Description abrt_anon_write (off , off) Allow ABRT to modify public files used for public file transfer services. abrt_handle_event (off , off) Determine whether ABRT can run in the abrt_handle_event_t domain to handle ABRT event scripts. abrt_upload_watch_anon_write (on , on) Determine whether abrt-handle-upload can modify public files used for public file transfer services in /var/spool/abrt-upload/. antivirus_can_scan_system (off , off) Allow antivirus programs to read non security files on a system ...
To set a boolean temporarily, run this command, where boolname is the name of the boolean and value is either on or 1, or off or 0.
setsebool boolname=value
To set it permanently, add the -P switch:
setsebool -P boolname=value
Conclusion
There are other functions you can perform with the SELinux Troubleshooter, such as creating a specific policy module for your own system. You might find this SELinux guide helpful for understanding those functions.
Photo by Cristina Gottardi on Unsplash






Matthew Bunt
Thank you. The linked video and this article really demystified SELinux for me.
Paul W. Frields
@Matthew: Glad to hear it! That video is really great. I know Thomas, the guy who delivered the talk, and he’s a total superstar.
Dmitry Minsky
There is also nice console tool called audit2why. You can search for suspicious entry in audit.log and transform it into human readable form.
Use example:
grep 1506354538.013:954 /var/log/audit/audit.log | audit2why
Maimela
good day, i will like to know if anyone has experienced a bug with dual booting. it’s been two weeks since i logged in windows 10, after login for a couple of hours when i returned to fedora, i might the grub boot error messages!!! please anyone help. i got fedora on multiple computers and ran the updates for 29 September and i don’t know if it was because of that or something wrong with win 10