What is encryption?
In cryptography, encryption is encoding information so that only authorized parties can read it. Encryption doesn’t necessarily prevent someone else from getting access to your data. However, if they do, it can prevent that data’s content from being read. Encryption transforms the intended information, referred to as plaintext, using an algorithm into ciphertext that’s only readable if decrypted.
Why should I encrypt?
Encryption is important because it allows you to securely protect data you don’t want anyone else to access. Businesses use encryption to protect corporate secrets. Governments use it to secure classified information. And many individuals use encryption to protect personal information, guard against identity theft, or wipe media before replacing it.
By default Fedora and most Linux Distribution come with LUKS, the Linux Unified Key Setup system. LUKS manages encryption on storage devices such as hard disks.
Cryptography lesson: Why use a strong passphrase?
This part’s for cryptography geeks. You need to set a strong passphrase because Fedora’s default implementation of LUKS uses AES-256 with a SHA-256 hashing to encrypt the disk volume. It also has a cipher feedback to help protect it from frequency attacks and others attacks that target statically encrypted data. As an algorithm, AES has been proven by cryptanalysis testing as secure. The weakness actually lies within the cipher and the software that passes keys to the cipher. Specifically, the risk lies in the keystore, which is stored in the header of the volume. The keystore is secured by a passphrase, which is open to things like dictionary or brute force attacks. If such an attack was successful at guessing your passphrase, it would decrypt the keystore. Using longer, more complex, non-word passwords reduces the chance of this happening.
Encrypting your Fedora system
Step One: Install Fedora 24 on 32 and 64-bit AMD and Intel
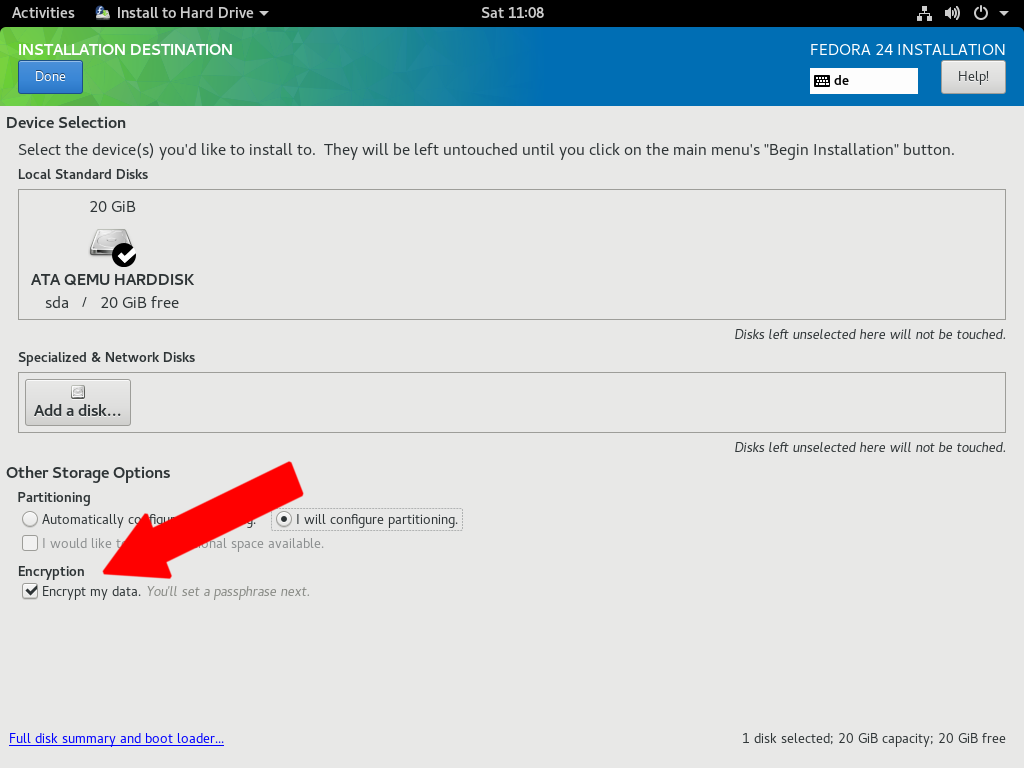
If you decide to encrypt your Fedora system’s storage, you can do so with the Anaconda installer during setup. Check the option for Encrypt my data.
After you confirm, you must create a an encryption passphrase. Note: The best encryption can be easily broken if you choose a weak password! Choose one easy for you to remember, but difficult for others to guess. Consider using a tool like KeePass or the pwgen command-line tool, which is described later.
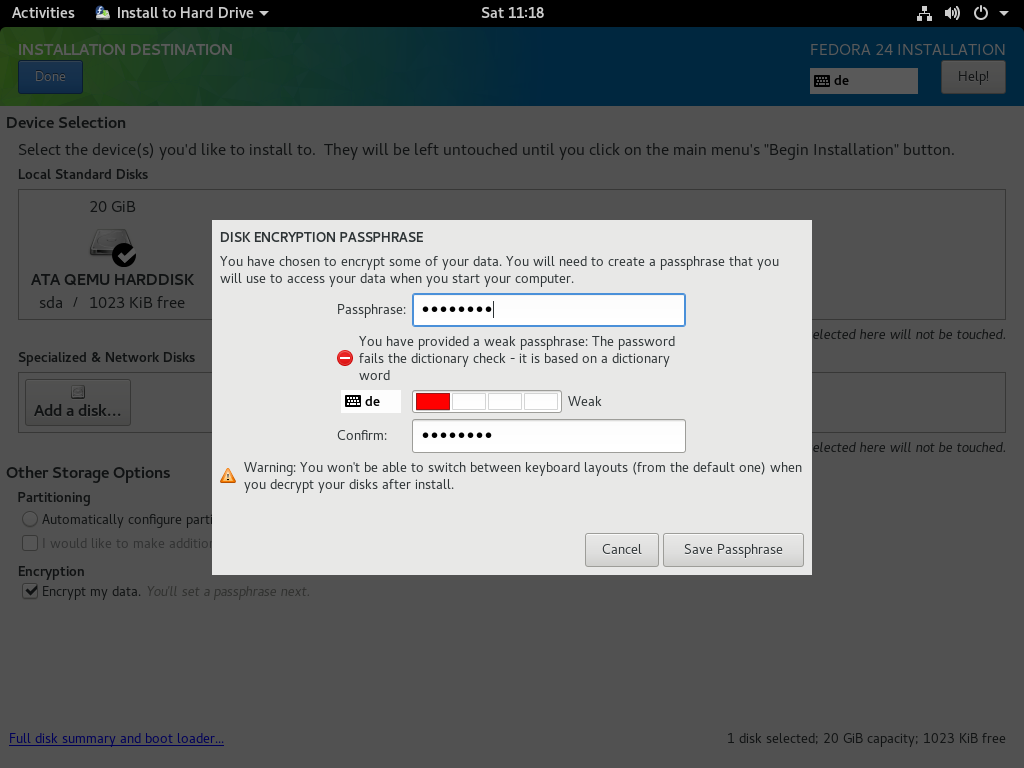
Step Two: Change your passphrase
If you’re unable to copy and paste a strong password, such as when using Virtual Machine Manager, choose a simple one and change it immediately after the first reboot. To replace your temporary password with a random passphrase, you can use the KeePass tool; alternatively, use the pwgen utility by running the following commands:
# dnf install pwgen -y # pwgen -C 10
Once you have your strong passphrase, run:
# cryptsetup luksAddKey /dev/sda2
The result should look something like this:
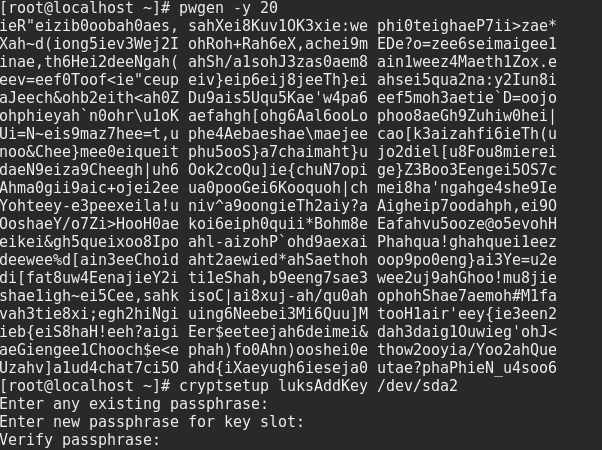
After you’ve added the new passphrase, kill the old/weak passphrase slot:
# cryptsetup luksKillSlot /dev/sda2 0
Then, to confirm, enter the strong passphrase you just added:
Learning more
For more information about encrypting your Fedora system at installation time, consider reviewing the official Installation Guide and the Disk Encryption User Guide on the Fedora Wiki.






pedro andrade
It would also be interesting if you showed how to encrypt your system if you have fedora already installed. if that’s even possible.
regards.
Andre Gompel
“Interesting if you showed how to encrypt your system if you have fedora already installed.”
Yes, you can,.
When done, in MATE’s CAJA (File manager) just click on the volume, etc..
Please post, if you find some innacuracy, or need to comment.
——————— HERE IS THE PROCEDURE ———–
== Create the block devices ==
Create the block devices you want to encrypt by using parted, pvcreate, lvcreate and mdadm.
== Optional: Fill the device with random data ==
dd if=/dev/urandom of=
Fastest way, which provides lower quality random data:
badblocks -c 10240 -s -w -t random -v
== Format the device as a dm-crypt/LUKS encrypted device == (Destructive)
cryptsetup luksFormat
== After supplying the passphrase twice the device will be formatted for use. To verify, use the following command: ==
cryptsetup isLuks && echo Success
== To see a summary of the encryption information for the device, use the following command: ==
sudo cryptsetup luksDump /dev/sda4
LUKS header information for /dev/sda4
Version: 1
Cipher name: aes
Cipher mode: xts-plain64
Hash spec: sha1
Payload offset: 4096
MK bits: 256
MK digest: 69 dd 64 20 55 fc 15 d7 58 d4 29 10 dc 85 b1 7f b5 62 06 1b
MK salt: 21 38 e0 d0 14 54 b6 eb 9e 43 a4 e3 6b df dc ef
5d e5 2b ff 63 eb 53 a6 f4 57 a2 9d 10 0e 01 19
MK iterations: 61750
UUID: 36aaabd9-c7fc-420a-8b57-316636428e44
Key Slot 0: ENABLED
Iterations: 251226
Salt: ea 3b a4 1a d1 31 6e 34 c0 33 88 0e 20 80 e0 df
ad 87 ae 15 3e 56 b5 ee c9 75 09 d0 82 90 2a 6d
Key material offset: 8
AF stripes: 4000
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
== Create a mapping to allow access to the device’s decrypted contents ==d
sudo cryptsetup luksUUID /dev/sda4
36aaabd9-c7fc-420a-8b57-316636428e44
sudo cryptsetup luksOpen /dev/sda4 MyLongPassPhrase
Enter passphrase for /dev/sda4:
<the paraphrase.
== Verify there is device info ==
There should now be a device node, /dev/mapper/, which represents the decrypted device. This block device can be read from and written to like any other unencrypted block device.
To see some information about the mapped device, use the following command:
sudo dmsetup info MyLongPassPhrase
== Create filesystems on the mapped device, or continue to build complex storage structures using the mapped device ==
sudo mkfs.xfs -f /dev/mapper/MyLongPassPhrase ## -f to force overwriting existing fs
== Mount on existing directory ==
sudo mount /dev/mapper/MyLongPassPhrase /mnt/test/
== Add the mapping information to /etc/crypttab ==
In order for the system to set up a mapping for the device, an entry must be present in the /etc/crypttab file. If the file doesn’t exist, create it and change the owner and group to root (root:root) and change the mode to 0744. Add a line to the file with the following format:
vivreHeureux 36aaabd9-c7fc-420a-8b57-316636428e44 none
== Add an entry to /etc/fstab ==
Add an entry to /etc/fstab. This is only necessary if you want to establish a persistent association between the device and a mountpoint. Use the decrypted device, /dev/mapper/ in the /etc/fstab file.
In many cases it is desirable to list devices in /etc/fstab by UUID or by a filesystem label. The main purpose of this is to provide a constant identifier in the event that the device name (eg: /dev/sda4) changes. LUKS device names in the form of /dev/mapper/luks- are based only on the device’s LUKS UUID, and are therefore guaranteed to remain constant. This fact makes them suitable for use in /etc/fstab.
Daniel Aleksandersen
Do keep in mind that it’s also very hard to recover data from an encrypted system. Be sure to also configure system and user data backups of any encrypted system. The GNOME Backup utility (Déjà Dup) can help you create encrypted backups on a schedule.
wigust
It’s a pain to recover in either way. Do backups whatever you use
Christophe GRENIER
PhotoRec (testdisk package or qphotorec for the GUI) can recover lost files from an unlocked encrypted LUKS filesystem. Instead of selecting the LUKS partition (ie. /dev/sda2), select the unlocked device (ie. /dev/mapper/home)
Andre Gompel
== Create the block devices ==
Create the block devices you want to encrypt by using parted, pvcreate, lvcreate and mdadm.
== Optional: Fill the device with random data ==
dd if=/dev/urandom of=
Fastest way, which provides lower quality random data:
badblocks -c 10240 -s -w -t random -v
== Format the device as a dm-crypt/LUKS encrypted device == (Destructive)
cryptsetup luksFormat
== After supplying the passphrase twice the device will be formatted for use. To verify, use the following command: ==
cryptsetup isLuks && echo Success
== To see a summary of the encryption information for the device, use the following command: ==
sudo cryptsetup luksDump /dev/sda4
LUKS header information for /dev/sda4
Version: 1
Cipher name: aes
Cipher mode: xts-plain64
Hash spec: sha1
Payload offset: 4096
MK bits: 256
MK digest: 69 dd 64 20 55 fc 15 d7 58 d4 29 10 dc 85 b1 7f b5 62 06 1b
MK salt: 21 38 e0 d0 14 54 b6 eb 9e 43 a4 e3 6b df dc ef
5d e5 2b ff 63 eb 53 a6 f4 57 a2 9d 10 0e 01 19
MK iterations: 61750
UUID: 36aaabd9-c7fc-420a-8b57-316636428e44
Key Slot 0: ENABLED
Iterations: 251226
Salt: ea 3b a4 1a d1 31 6e 34 c0 33 88 0e 20 80 e0 df
ad 87 ae 15 3e 56 b5 ee c9 75 09 d0 82 90 2a 6d
Key material offset: 8
AF stripes: 4000
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
== Create a mapping to allow access to the device’s decrypted contents ==d
sudo cryptsetup luksUUID /dev/sda4
36aaabd9-c7fc-420a-8b57-316636428e44
sudo cryptsetup luksOpen /dev/sda4 vivreHeureux
Enter passphrase for /dev/sda4:
<the paraphrase.
== Verify there is device info ==
There should now be a device node, /dev/mapper/, which represents the decrypted device. This block device can be read from and written to like any other unencrypted block device.
To see some information about the mapped device, use the following command:
sudo dmsetup info vivreHeureux
== Create filesystems on the mapped device, or continue to build complex storage structures using the mapped device ==
sudo mkfs.xfs -f /dev/mapper/vivreHeureux ## -f to force overwriting existing fs
== Mount on existing directory ==
sudo mount /dev/mapper/vivreHeureux /mnt/test/
== Add the mapping information to /etc/crypttab ==
In order for the system to set up a mapping for the device, an entry must be present in the /etc/crypttab file. If the file doesn’t exist, create it and change the owner and group to root (root:root) and change the mode to 0744. Add a line to the file with the following format:
vivreHeureux 36aaabd9-c7fc-420a-8b57-316636428e44 none
== Add an entry to /etc/fstab ==
Add an entry to /etc/fstab. This is only necessary if you want to establish a persistent association between the device and a mountpoint. Use the decrypted device, /dev/mapper/ in the /etc/fstab file.
In many cases it is desirable to list devices in /etc/fstab by UUID or by a filesystem label. The main purpose of this is to provide a constant identifier in the event that the device name (eg: /dev/sda4) changes. LUKS device names in the form of /dev/mapper/luks- are based only on the device’s LUKS UUID, and are therefore guaranteed to remain constant. This fact makes them suitable for use in /etc/fstab.
someone
You should be recommending diceware for secure, memorable passphrases:
https://en.wikipedia.org/wiki/Diceware
Dylanger Daly
Also just know, the master key sits in memory on a running live system, watch out for DMA attacks.
Hugo
Very interesting article. The issue of encryption today is very important, but fedora follows must deliver good documentation to use it properly in different combinations. For example, the article recommended at the end is obsolete (shows a warning when entering the Wiki).
Related topics I’d like to see in Fedora Magazine:
• Encrypting drives in older installations
• Encrypt external drives
• Use gnome-disk-utility to encrypt partitions and external devices (and use custom file systems)
Cheers
Joe
Folks;
The nomenclature for fsck operations on lvm installations seems a bit rough. I recently lost access to a device used to store Evolution backups that are locked behind LUKS and found myself fumbling!