Keybase is a service that makes a security web of trust usable for everyone. It uses encryption to provide secure communications — including chat, file sharing, and publishing documents. But it extends encryption into a social context, like Github or Gitlab do for project and source code control. Like other acceptable secure systems, Keybase doesn’t rely on secret source code, and is based on free software.
Proving your identity
Most people use some form of social network today. Quite a few of these are already supported, including:
- Github
- …and more
Proving the authenticity of a social account or site involves posting special coded information. These proofs show that an account or site truly belongs to you. Then other users can also verify your identity through these proofs. Arbitrary websites under your control are also supported.
The proofs are stored in a blockchain that ensures integrity and authenticity as you make changes.
Getting started with Keybase.io
To get started, download and install the package for your system. This example assumes you have an Intel 64-bit processor, like most computers today. If you have a very old 32-bit system, use i386 instead of amd64 below. The package takes some time to download, depending on your internet connection speed.
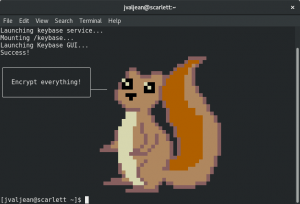
Now run the initial startup application:
The following screen appears, encouraging you to use encryption.
The following window appears if you’re running a graphical desktop:
If you have an account on Keybase.io, you can sign in using the app window that appears. You can also create a new account.
When you create a new account, you’re asked to name the computer from which you’re using the service. That way the service can alert you if there’s a login from a new device.
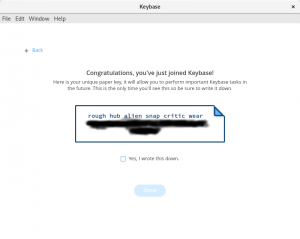
You’ll also receive a special proof that you should write down and store in a secure location. It will look similar to this:
This default proof is recorded like other devices or computers where you log in. It lets you access your Keybase account from another computer in case your known computers are lost, broken, or stolen. The long list of words makes the proof easy to type in, but very hard to guess.
To prove an additional service or site is authentically yours, select the Prove function and follow the instructions. The instructions will differ depending on the nature of the service or site. The more sites you prove, the better the level of authenticity you’re providing.
If you’re not running a graphical desktop, or prefer the terminal, type this to see a list of available commands:
keybase help
If you want to prove more services, for example, run the keybase prove command. For help with a specific command such as prove, type:
keybase help prove
Making crypto social
If you’re using Fedora Workstation, notice a Keybase icon appears in the extra status icon tray at the bottom left of your screen. Select it to bring up the main app window. From this window, you can carry out different secure tasks.
By default, the window shows your encrypted folders. These are stored on your system using a FUSE plugin, and you can access them through the /keybase path. You can use these folders just like any other folder on your system. When you store documents there, they are automatically encrypted. Items in the public folder are available for others on Keybase to see. The other users can be certain these documents are authentic, thanks to the way GPG encryption and signing work.
When you select the people icon, your profile window appears. From this window you can access your list of followers and those you’re following on Keybase. “Following” is the Keybase expression of verifying identity.
Using the Keybase main window, you can share files with other users either publicly or privately. Users signed into Keybase receive notifications when new files are shared to them or the contents of a shared folder change. You can also enjoy encrypted chat with other users with whom you’re connected.
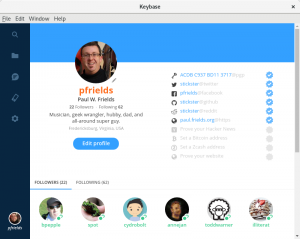
You’ll know when someone shares files or chats with you that they’re really who they claim to be. In part this is because they’ve verified their identity based on social accounts and properties. Because many other Keybase users recognize those accounts you can be more certain of their identity.







Jose
Interesting, But must include Whats app tool for PC
Paul W. Frields
@Jose: As far as I can tell, Whatsapp is not open source. Therefore it will not be included in Fedora, period. Please re-read our mission statement: https://fedoraproject.org/wiki/Overview
janvlug
Can you elaborate on this? Does installing the keybase rpm pull in proprietary code on your Fedora system?
Shakhar Dasgupta
I just tried it out. Do you know if the PGP option is safe? It seems to be sending my private key to the servers, although it’s encrypted.
Paul W. Frields
@Shakhar: The key is encrypted before sending. AIUI it can’t be feasibly decrypted by Keybase or anyone else who can access the blockchain. I’m not a crypto expert though, so you can consult Keybase about it.
Daniel
You have the option of removing your private key on Keybase’s servers. I thought it was weird that they recommend this.
Juan Miguel Navarro Martínez
You don’t need to send your PGP private key to their servers, that will leave you with no ability to PGP sign on the tools in their website but you’ll still be able to PGP sign with
on CLI.
Same goes for PGP decrypting on their website, you can still do it on the CLI tool.
Brian
There is an option to avoid importing your key and instead copy and paste gpg commands to sign keybase changes.
This feature is important to me since I have a Yubikey Neo acting as a PGP card, so I have no private key to upload. It’s all locked into the hardware.
Todd
I’ve been using keybase for quite some time now. It’s an outstanding service. I use their Keybase filesystem extensively and secure chat for specific use cases.
I’ll be curious where they take it in the future. It needs mobile at some point and other things to de-geek it, but thus far… It’s a solid service.
Edward
I think Fedora should package up riot.im and get it into the official repos.
Ush Feeley
It makes sense to verify that the package is at least un-tampered with betweeen the keybase web server and you:
Download keybase code signing key
wget https://keybase.io/docs/server_security/code_signing_key.asc
Verify the fingerprint on the code signing key
https://keybase.io/docs/server_security/our_code_signing_key
gpg –with-fingerprint code_signing_key.asc
pub 4096R/656D16C7 2013-11-19 Keybase.io Code Signing (v1) code@keybase.io
Key fingerprint = 222B 85B0 F90B E2D2 4CFE B93F 4748 4E50 656D 16C7
Import the code signing key to RPM
rpm –import code_signing_key.asc
Download the package from above
Check that the package is signed with keybase code signing key
$ rpmkeys -K keybase_amd64.rpm
keybase_amd64.rpm: (RSA) sha1 ((MD5) PGP) md5 NOT OK (MISSING KEYS: RSA#656d16c7 (MD5) PGP#656d16c7)
Then, and only then install the package
Ush Feeley
Bah… seems to have eaten some of my formatting:
sudo rpmkeys -K keybase_amd64.rpm
keybase_amd64.rpm: rsa sha1 (md5) pgp md5 OK