Nextcloud is a software suite for storing and syncing your data across multiple devices. You can learn more about Nextcloud Server’s features from https://github.com/nextcloud/server.
This article demonstrates how to build a personal cloud using Fedora and Nextcloud in a few simple steps. For this tutorial you will need a dedicated computer or a virtual machine running Fedora 31 server edition and an internet connection.
Step 1: Install the prerequisites
Before installing and configuring Nextcloud, a few prerequisites must be satisfied.
First, install Apache web server:
# dnf install httpd
Next, install PHP and some additional modules. Make sure that the PHP version being installed meets Nextcloud’s requirements:
# dnf install php php-gd php-mbstring php-intl php-pecl-apcu php-mysqlnd php-pecl-redis php-opcache php-imagick php-zip php-process
After PHP is installed enable and start the Apache web server:
# systemctl enable --now httpd
Next, allow HTTP traffic through the firewall:
# firewall-cmd --permanent --add-service=http
# firewall-cmd --reload
Next, install the MariaDB server and client:
# dnf install mariadb mariadb-server
Then enable and start the MariaDB server:
# systemctl enable --now mariadb
Now that MariaDB is running on your server, you can run the mysql_secure_installation command to secure it:
# mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL
MariaDB SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP
CAREFULLY!
In order to log into MariaDB to secure it, we'll need the
current password for the root user. If you've just installed
MariaDB, and you haven't set the root password yet, the password
will be blank, so you should just press enter here.
Enter current password for root (enter for none): <ENTER>
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into
the MariaDB root user without the proper authorization.
Set root password? [Y/n] <ENTER>
New password: Your_Password_Here
Re-enter new password: Your_Password_Here
Password updated successfully!
Reloading privilege tables...
... Success!
By default, a MariaDB installation has an anonymous user,
allowing anyone to log into MariaDB without having to have
a user account created for them. This is intended only for
testing, and to make the installation go a bit smoother. You
should remove them before moving into a production environment.
Remove anonymous users? [Y/n] <ENTER>
... Success!
Normally, root should only be allowed to connect from
'localhost'. This ensures that someone cannot guess at the
root password from the network.
Disallow root login remotely? [Y/n] <ENTER>
... Success!
By default, MariaDB comes with a database named 'test' that
anyone can access. This is also intended only for testing, and
should be removed before moving into a production environment.
Remove test database and access to it? [Y/n] <ENTER>
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes
made so far will take effect immediately.
Reload privilege tables now? [Y/n] <ENTER>
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your
MariaDB installation should now be secure.
Thanks for using MariaDB!
Next, create a dedicated user and database for your Nextcloud instance:
# mysql -p > create database nextcloud; > create user 'nc_admin'@'localhost' identified by 'SeCrEt'; > grant all privileges on nextcloud.* to 'nc_admin'@'localhost'; > flush privileges; > exit;
Step 2: Install Nextcloud Server
Now that the prerequisites for your Nextcloud installation have been satisfied, download and unzip the Nextcloud archive:
# wget https://download.nextcloud.com/server/releases/nextcloud-17.0.2.zip # unzip nextcloud-17.0.2.zip -d /var/www/html/
Next, create a data folder and grant Apache read and write access to the nextcloud directory tree:
# mkdir /var/www/html/nextcloud/data # chown -R apache:apache /var/www/html/nextcloud
SELinux must be configured to work with Nextcloud. The basic commands are those bellow, but a lot more, by features used on nexcloud installation, are posted here: Nextcloud SELinux configuration
# semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/html/nextcloud/config(/.*)?' # semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/html/nextcloud/apps(/.*)?' # semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/html/nextcloud/data(/.*)?' # semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/html/nextcloud/.user.ini' # semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/html/nextcloud/3rdparty/aws/aws-sdk-php/src/data/logs(/.*)?' # restorecon -Rv '/var/www/html/nextcloud/'
Step 3: Configure Nextcloud
Nextcloud can be configured using its web interface or from the command line.
Using the web interface
From your favorite browser, access http://your_server_ip/nextcloud and fill the fields:
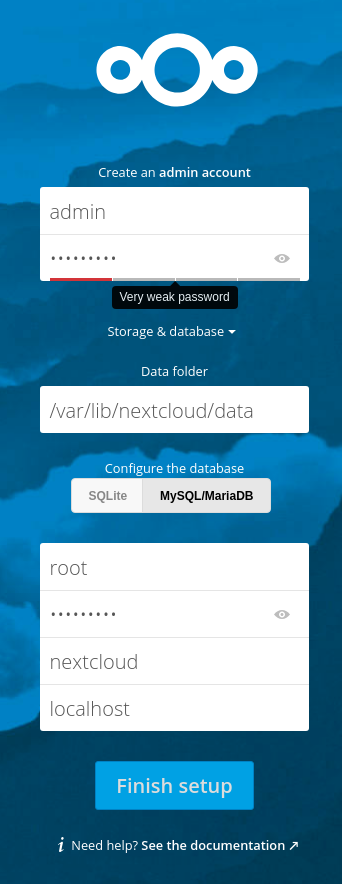
Using the command line
From the command line, just enter the following, substituting the values you used when you created a dedicated Nextcloud user in MariaDB earlier:
# sudo -u apache php occ maintenance:install --data-dir /var/www/html/nextcloud/data/ --database "mysql" --database-name "nextcloud" --database-user "nc_admin" --database-pass "DB_SeCuRe_PaSsWoRd" --admin-user "admin" --admin-pass "Admin_SeCuRe_PaSsWoRd"
Final Notes
- I used the http protocol, but Nextcloud also works over https. I might write a follow-up about securing Nextcloud in a future article.
- I disabled SELinux, but your server will be more secure if you configure it.
- The recommend PHP memory limit for Nextcloud is 512M. To change it, edit the memory_limit variable in the /etc/php.ini configuration file and restart your httpd service.
- By default, the web interface can only be accessed using the http://localhost/ URL. If you want to allow access using other domain names, you can do so by editing the /var/www/html/nextcloud/config/config.php file. The * character can be used to bypass the domain name restriction and allow the use of any URL that resolves to one of your server’s IP addresses.
'trusted_domains' =>
array (
0 => 'localhost',
1 => '*',
),
— Updated on January 28th, 2020 to include SELinux configuration —






Markus
Ok there’s a little thing I take issue with here. It is never acceptable to disable SELinux.
Please update this guide (which seems to be slightly edited copypasta) to actually include the very few very simple steps to ensure functionality with SELinux enabled.
There’s a big problem on the internet that many guides starts with disabling SELinux and I think Fedora Magazine should be part of educating people on good practices instead of being part of the problem.
Ahmed
Absolutely right! Security should be number one priority.
Tijmen
Agreed!
Robin Lee
Nextcloud is great. I already run my own instance. But the problem is connecting to it. I have NC running on a server at home and only reachable by the world as a hidden service i.e. through an .onion-address. I can access my own NC from my laptop anywhere in the world with the Tor browser. Unfortunately Gnome desktop is really bad at handling .onion-addresses though. Wish that would improve
Jan
Great to see Nextcloud get some attention! It is a great project and has all the features you could ever want from a personal cloud.
I have been a bit disappointed with the Nextcloud hosting providers, so I might use this guide in the future.
If you are going to continue with a writeup, could you elaborate on how to install HTTPS certificates on the server, for best security?
qoheniac
There is also this cool project that adds some convenience tools around Nextcloud and ships everything as a Docker container: https://ownyourbits.com/2017/11/15/nextcloudpi-dockers-for-x86-and-arm/
Damien Dye
I recommend usign php-fpm rather than mod_php in apache.
php-fpm is much better at resource control that impact both ram and CPU performace.
Stuart D Gathman
What is the advantage of nextcloud over owncloud (which is already packaged for Fedora)? Is there a Fedora packaging effort underway for nextcloud?
Rhea
Nextcloud can not be repackaged (it is packaged in fact) with latest version due to no upgrade path to it. It’s stuck, it’s been stuck for a few years now with many discussions how to solve it, so far without a result. Nextcloud is developed by the original authors of Owncloud but with less business-only features and restrictions and better licensing – see their presentation at FOSDEM 2018: https://archive.fosdem.org/2018/schedule/event/nextcloud
Forther note that Owncloud is also out of date in Fedora with packaged version 9.1 (.fc28!!) and latest 10.8
Do not take either from Fedora repositories or you will lose your data when you will decide to upgrade to the latest. There is no upgrade path for either.
Eric Nicholls
Owncloud is like Open Office in the Linux world. The project was acquired by a for profit company, so even the original developer moved to a more community friendly environment.
So nextcloud is more like LibreOffice.
Rohit
Stop disabling SELinux D: —
http://tag1consulting.com/blog/stop-disabling-selinux
Curt Warfield
Hi,
It’s not a good idea to disable SELinux and our recommended practice is to always have it in enforcing mode.
Pete Thorsen Jr
First, let me say this, I could be wrong but in my humble opinion it’s wrong to have folks disable SELinux and use the http protocol instead of the https protocol.
Wouldn’t it have been better to include those and make the article better from a security aspect? I know it would have made it longer also but I am not aware of any kind of article length restriction. Of is there?
I’m just saying …
Héctor Louzao
There is a discussion in fedora devel-list about that:
https://lists.fedoraproject.org/archives/list/devel@lists.fedoraproject.org/thread/R2DBDLZAUSV7S6PBQS5GX44SNC7S3GPL/
Regards.,
Scott Trakker
Great article!
This is definitely something I want to do in the future!
My ideal setup would be:
Fedora CoreOS
NextCloud Hub
LibreOffice Online
This way we have the perfect modern open source home server!!
Could you (in the future) also write an article with Fedora CoreOS?
Joe Fidler
Thank you very much for documenting this setup. I rely on both Fedora and NextCloud, so I see needing this in my future.
Astor D
Thanks for writing this article. It is very useful. An “https” follow-up would be greatly appreciated.
Stan
I cant accept the fact that disabling SELinux is a step of the article? I see the link of how to configure it, but I think it should be the other way – the article should have the steps, how to configure it and a link, how to disable it. I never disable SELinux and take the extra 15 minutes to configure it and I believe that should be the recommended way to install anything on Fedora/CentOS/etc
David Juran
Both NextCloud and OwnCloud are packaged in Fedora but unfortunately both are more or less abandoned. A volunteer to help out maintaining those would be much appreciated
Narcis
Maybe this link will answer few questions:
https://civihosting.com/blog/nextcloud-vs-owncloud/
Mario
Does it, in 2020, make sense to make tutorials like these for installing software on a box rather than just using Docker (or Podman for that matter)?
NextCloud has an official image: https://github.com/nextcloud/docker
Note, this is not so much criticism as it is a question 🙂
D
I totally agree with Mario.
Especially in the case of nextcloud it would be very helpful to have a documented away to configure the various containers required on Fedora with podman.
It’s a non-trivial task if you don’t compromise on security and actually set up CA signed SSL certificates with a reverse proxy
Mark
I Use OwnCloud currently, although thanks to the link posted by Narcis I will look into NextCloud. However…
OwnCloud client files are still usable in F31, although it is smart enough to irritatingly notify that updates are available.
The OwnCloud server component (owncloud-files) also works on F31, if you use rpm to remove all the ones installed from the Fedora repositories and download the packages the supported location https://download.owncloud.org/download/repositories/production/owncloud/ so there is an update path; if you keep away from the fedora repos; as mentioned by Rhea in an earlier reply the packages in the fedora repos do not work.
I would argue against packaging NextCloud in Fedora repositories for the same reason the OwnCloud server component does not work correctly from Fedora repositories; package maintainers have no reason to keep up with the fast pace of changes in Fedora; if a build works on ubuntu/mint/bsd/fedora and a change in fedora breaks it on fedora why would any developer risk changing a working code base because fedora changed the rules (remember they are not being paid by fedora users to support this free software, if it works on the majority of linux OS’s they are not going to change it because a change in fedora breaks it). Packages disappear from (or simply stop working from) the Fedora repos with every Fedora update so the reply earlier that the version of owncloud in the fedora repos does not work is to be expected rather than a surprise.
Apart from that, I mentioned the OwnCloud client packaged with the Fedora31 repos still worked and it slots nicely into the gnome file manager so I have a big green tick on owncloud and dropbox folders when seen from the file manager; in fact I use the Fedora client to sync files between a combination of F30 and F31 desktops via my local owncloud server.
The point of the above paragraph is that this post is about setting up the server side of NextCloud. Nice but totally useless to have a server side without integrated client software.
It would be useful if a followup up post (or addition to this post) on what desktop clients are available to use with NextCloud for those like me that have never heard of it.
For example as it is based on OwnCloud will the existing OwnCloud clients in the Fedora repos be able to sync files in the background via a NextCloud server or are there separate clients readers of the post need to be aware of.
On the many comments on the preference to never disable SELinux I agree. If it was a package in a repo I would expect a SELinux policy to be available and installed as part of the package if it was needed for the application to work; absence of a policy for any application (writing a policy is simple) implies they are not quite sure how it works.
Rhea
Maybe there is upgrade path for Owncloud for now, but not for long. You can’t upgrade cross-major versions. That was what I meant, Nextcloud in Fedora is several major versions behind. Owncloud will get to the same situation sooner or later – it wasn’t updated in something like two years now.
Mark
Thanks Rhea for clarifying.
You are also correct on OwnCloud not being updated for a few years, and it simply not working on any OS with an up-to-date version of php for over a year before they got around to updating the app which was a major pain for me.
An interesting observation you made that the NextCloud packages available in the repositories are also a few major versions behind, which I guess is why the article downloads them directly from the nextcloud site. For users that may do a ‘dnf search nextcloud’ note Rheas comment above and don’t use the packages but follow the instructions in the article instead.
With any app sourced from other than the Fedora repo you cannot guarantee it will keep working with Fedora which is to be expected; as long as users expect that installing packages like NextCloud as discussed in this article should be embraced by users for the short term functionality gained, as long as they do not rely on it.
Although it always supprises me the number of packages in the Fedora repos that just do not work on Fedora anymore.
K. de Jong
Why isn’t my comment approved? I also think it’s not acceptable for Fedora to publish a guide which starts with disabling SELinux.
Thomas Klein
Thanks for including the steps regading SELinux! I remember that was a bit on the trick side (even with the help of NC readmes) when I had to find out how to do this for running NC on my Fedora Server. Disabling SELinux, like most of us have agreed here, is not an option. Certainly not for a server 🙂
Regarding SSL certificates, I have this up and running with let’s encrypt certbot, deployed on nginx, serving NC and WordPress. And it was a PITA to get this working for someone like me who still feels like a “newbie” on Linux and with web servers.
I was about to write an article here about the whole shebang, but am still reluctant to do so, as I still feel I’m not a savvy linux user who knows what he’s doing and who should tell more experienced people how to setup somthing 😉
Anyways, to whom it may concern, here’s how to run NC with letsencrypt certificates. Your mileage may vary as it is based on nginx running on ubuntu. Sigh.
https://draculaservers.com/tutorials/install-nextcloud-nginx-ubuntu/
You probably are lucky with searching on Google for a combination of keywords that suits your intended setup like “apache letsencrypt fedora” etc. Cheers, Thomas
J.Goutin
Nextcloud works well on Fedora. have been using it daily for and that I am very happy with it.
Concerning the setup, I personally use Ansible to deploy and fully configure Nextcloud.
I have an Ansible role here if somebody is interested (Part of a larger collection for Fedora): https://github.com/JGoutin/ansible_home/tree/master/roles/nextcloud
Vic
Hi,
After you edit the article to use SELinux, you let this line:
“I disabled SELinux, but your server will be more secure if you configure it.”
Thanks for the article !
dffr
this is not cloud, this is web serwer with some functionality
cloud are morre, more
diskless machine, etc
Felix Calderon
Please help with:
Could not open input file: occ
P-Kay
I prefer docker-compose. There are some official examples on https://github.com/nextcloud/docker/tree/master/.examples (insecure or with nginx proxy). Works fine, also with LDAPS (LDAP SSL). Just take not the alpine nextcloud image and copy the certs via bash.