In June of 2020, we published an article related to running Docker and Fedora 32. We described various workarounds that were required to run Docker, and we explained the bothersome situation at that time. But Docker has evolved, and it’s time to return to our previous tutorial. Thus, today we’ll talk about using Docker on Fedora Linux 35.
With this guide, you should be able to easily recreate an existing development environment, without having to retool your entire pipeline. We’ll focus on getting the right packages, testing a few important scenarios, and helping you with tooling.
Also a big shout-out to Mehdi Haghgoo, who previously published an article about using Podman as the foundation of docker-compose, and a great article about using Podman instead.
At the time of writing, Fedora 35 is just on the horizon, but not out yet. This guide is fully compatible with Fedora 34, and has been checked on both versions before publication.
Installation
Let’s start by stating that the two biggest issues of Docker on Fedora 32 are no longer relevant. Docker now supports CGroups v2 and NFTables, which makes this second guide considerably shorter. There are two ways of installing Docker on Fedora Linux, both giving the same end-result but offering different benefits.
Fedora’s way
There is a lot to unravel in the landscape of Docker. The Docker Engine is FLOSS and it’s also available as a package directly from Fedora’s repositories. This package is called Moby, as reference to the mascot of Docker. To install and enable that version, you can use the following commands:
$ sudo dnf install moby-engine docker-compose
$ sudo systemctl enable docker
This will give you all the tools you need and it will make sure that the Docker service starts whenever you start your computer.
$ sudo groupadd docker
$ sudo usermod -aG docker $USER
Docker is a system-wide service, which has itself root permissions and which also requires root-permissions to interact with. For a developer, it’s normally not a big risk to add yourself to the ‘docker’-group, so that you don’t have to type ‘sudo’ whenever interacting with Docker.
$ sudo systemctl reboot
Finish the short installation by restarting the computer.
Benefits
The Moby Engine version does not entail any possible license restrictions. No fees or subscriptions apply, now or in the future. There is also the benefit of system integration: The package maintainers of the Moby Engine can ensure that the package has the same high standard as all other packages on Fedora. Last but not least, Moby is also available for Fedora’s beta versions and Fedora Rawhide.
Docker’s way
Docker Inc. provides an official RPM Repository for the Docker Engine, including installation instructions. Do make sure that you only install one version at the time.
https://docs.docker.com/engine/install/fedora/
Docker Inc. normally releases support for the next version of Fedora Linux, a few weeks after the official release. If you're following this guide using a Fedora Beta, you'll have to stick with Moby.
Benefits
Using the official package has some benefits, as they can provide you with direct commercial support and certification. It also allows you to run Docker’s development or testing branch. Last but not least, it comes with older versions of certain dependencies, which might be interesting in some very exotic situations.
Upgrading
Chances are, that you’ve been running Docker since Fedora 32. In that case, you must remove the workarounds that were previously required.
$ sudo grubby --update-kernel=ALL --remove-args="systemd.unified_cgroup_hierarchy=0"
Docker required this workaround since Docker didn’t support CGroups V2, but that issue got addressed with Docker 20.10. Running this command will otherwise have no ill effect.
$ sudo firewall-cmd --permanent --zone=trusted --remove-interface=docker0 $ sudo firewall-cmd --permanent --zone=FedoraWorkstation --remove-masquerade
This will remove the unnecessary firewall configuration that was necessary for NFTables. Docker on Fedora 35 should have it’s own zone, and running these commands on an existing set-up should have no ill effects.
Usage
Time to get our hands dirty. We’ll do some tests to see the power of containers, and to see the entire system in action.
Hello World
You should have a running docker.service, which can create and start images for you. Test this by doing the following.
$ docker run hello-world
Now that Docker greets you, it’s also time to move on and to try something more advanced. Don’t forget that if you’re unsure about something, you can always check the staggering amount of official documentation on Docker.
Testing with Rawhide
For the next quick demonstration, we’ll make our own ‘hello world’ example, in which you’re free to play around. First, let’s create a folder to work from.
$ mkdir docker-tests $ cd docker-tests
then, make two files we need for this demonstration.
./docker-tests/ ├── dockerfile └── hello-rawhide.sh
./docker-tests/dockerfile
FROM fedora:rawhide COPY ./hello-rawhide.sh ./ RUN chmod +x ./hello-rawhide.sh ENTRYPOINT ["./hello-rawhide.sh"]
./docker-tests/hello-rawhide.sh
#!/usr/bin/env bash echo 'Talking to you from Fedora Rawhide' cat /etc/os-release
With those preparations done, build and run your own image using the following command. The -t parameter provides your image with a convenient name to use. If something goes wrong, make sure that the test files are not directly in your Home directory and check the spelling. Also, check that your terminal is in the correct folder.
[docker-tests]$ docker build -t rawhide-hello . [docker-tests]$ docker run rawhide-hello
This should give you some basic information about the container you’ve just build. Look at the ‘VARIANT’ value and see that you’ve successfully build a container image.
Composing a project
It is often required to start multiple containers at once. This can help you with software development, or it can create an entire application with all its dependencies. Let’s use a tutorial from docker-compose to illustrate this process with WordPress.
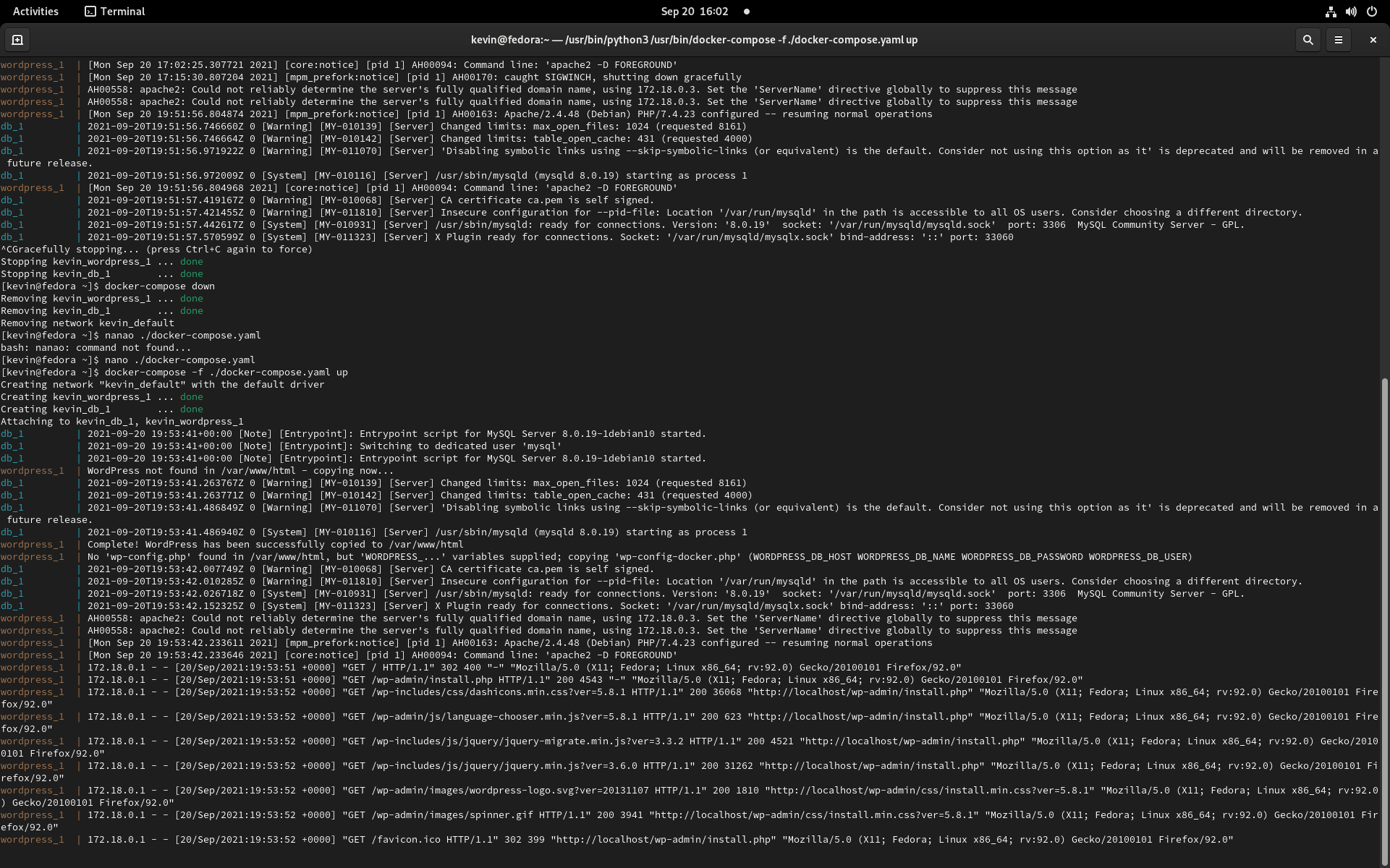
$ curl -o docker-compose.yaml \ https://raw.githubusercontent.com/docker/awesome-compose/master/wordpress-mysql/docker-compose.yaml $ docker-compose -f ./docker-compose.yaml up
If you now open your browser at http://localhost:80, you’ll be able to enjoy your own WordPress. The docker-compose file tells you how to combine multiple docker images, and how everything should be networked and stored. Powerful stuff.
If you keep the terminal window open, you can see the system logs. For example, you can see a log entry from Apache telling that they served a page on localhost. For more examples, you should check out the awesome-docker documentation project. To shut the demonstration down, you’ll have to do two things:
ctrl-c to abort the current terminal process $ docker-compose -f ./docker-compose.yaml down
Getting a UI
If you have experience with Docker on Mac OS or Windows, you’ll likely be accustomed to using Docker Desktop. Docker Desktop is a proprietary application that manages a virtual-machine for you, which then allows you to use the moby-engine on non-Linux platforms. Since such a VM is not necessary on Linux, there is no proprietary GUI application. There are some tools available to manage the moby-engine on Linux, both commercial, free and FLOSS, but there is no generic solution.
Lazy Docker
Lazy Docker is a light yet powerful tool to manage Docker containers. With the gracious help of our community member Atim, it’s possible to easily install and update Lazy Docker using Copr.
$ sudo dnf copr enable atim/lazydocker
$ sudo dnf install lazydocker
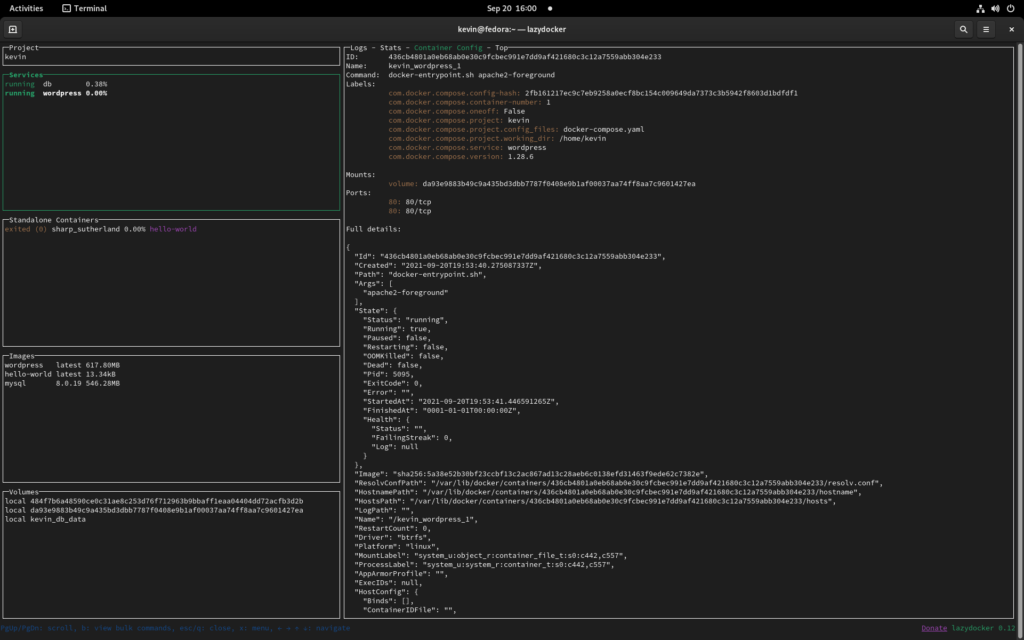
For more information and guides related to Lazy Docker, I would recommend you to check out their documentation and project page. Also don’t forget that since Lazy Docker is a Terminal UI application, you can also use it on machines that you can otherwise only access through an SSH connection.
Editor Plugin
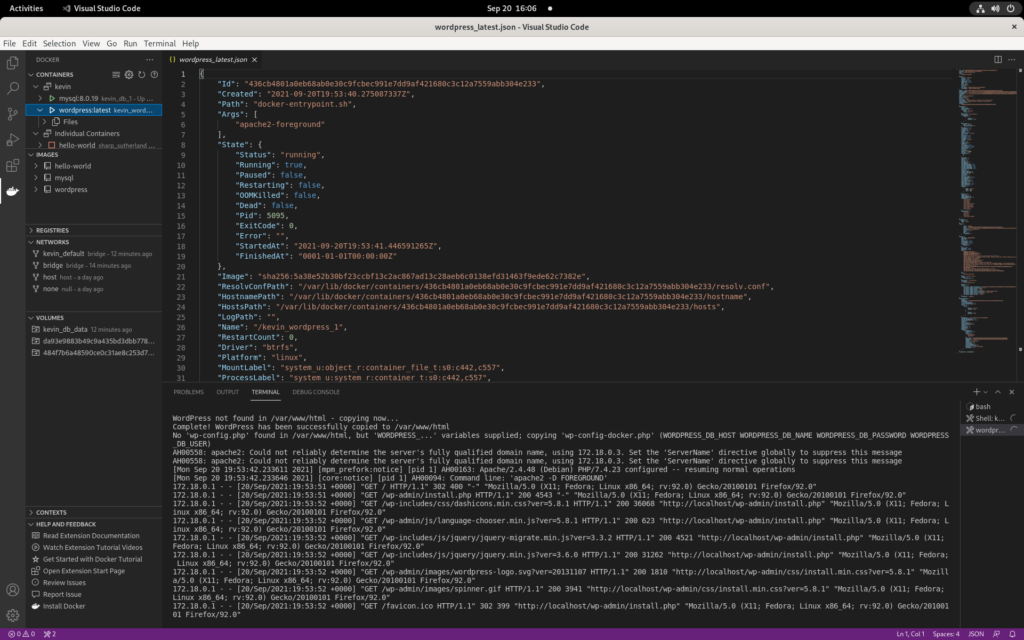
Another popular way of seeing the innards of your containers, is by using the Docker plugin for VS Code or VS Codium. While there would certainly be room for some extra bells and whistles, this UI should help you understand the relations between images, containers, and volumes.
At the time of writing, VS Code and Codium are not yet compatible with Fedora 35 Beta.
Summary
Linux containerization is a great technology, and it encapsulates some of the best aspects of modern software development. It allows you to build and control an entire software stack on Linux, Mac and Windows at the same time, from development all the way into production.
As a Fedora use, you can choose Moby, and you’ll even get some extra benefits:
- Fully compatible with Docker
- No hidden terms-and-conditions
- Integrate and update directly with Fedora Linux
- Ready for any future Beta and/or Rawhide channels






Eric
Hi good to know for developers using docker in their workflow. Thanks!
Mattias Bengtsson
Suggesting people to add themselves to the docker group seems pretty irresponsible to be honest.
Valo
Docker itself suggest this in their docs https://docs.docker.com/engine/install/linux-postinstall/
I think that it’s well redacted to let the reader know that a developer could benefit from this, not a deployed container in prod. 🙂
Vishal Raj
Great. Here’s my small article related to docker and local development – https://dev.to/vishalraj82/using-https-in-docker-for-local-development-nc7
Titouan Bénard
I am using VScode on Fedora 35 and VScode work fine
Cédric
And just use Podman if you care about security.
Renich
😀
I hear you!
Tomasz Gąsior
Don’t add your user account to
group. This makes your OS very insecure making docker working kinda like sudo but without any password restriction. Malicious software is able to get root permissions this way and attack your workstation.
Also, you may want to use
instead just
. This will make Docker starting the first time you use it instead just always when OS is starting, making boot time faster.
Renich
👍
Anders F Björklund
See https://docs.docker.com/engine/security/rootless/
for how to run the docker daemon more like podman…
Ivo
or just go with a podman 😉
RobertR
Podman is OK, unless, for example, you want to start learning terraform with docker. It is possible point terraform to podman’s socket, but it doesn’t work seamlessly.
Mebus
Hi folks,
I tried this on Fedora 34 and I got this error:
Okt 23 11:12:50 box dockerd[6252]: failed to start daemon: Error initializing network controller: Error creating default “bridge” network: Failed to program NAT chain: COMMAND_FAILED: ‘python-nftables’ failed:
Okt 23 11:12:50 box dockerd[6252]: JSON blob:
Okt 23 11:12:50 box dockerd[6252]: {“nftables”: [{“metainfo”: {“json_schema_version”: 1}}, {“insert”: {“rule”: {“family”: “inet”, “table”: “firewalld”, “chain”: “filter_INPUT_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “iifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “filter_IN_docker”}}]}}}, {“insert”: {“rule”: {“family”: “inet”, “table”: “firewalld”, “chain”: “filter_FORWARD_OUT_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “oifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “filter_FWDO_docker”}}]}}}, {“insert”: {“rule”: {“family”: “ip”, “table”: “firewalld”, “chain”: “nat_POSTROUTING_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “oifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “nat_POST_docker”}}]}}}, {“insert”: {“rule”: {“family”: “ip6”, “table”: “firewalld”, “chain”: “nat_POSTROUTING_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “oifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “nat_POST_docker”}}]}}}, {“insert”: {“rule”: {“family”: “inet”, “table”: “firewalld”, “chain”: “filter_FORWARD_IN_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “iifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “filter_FWDI_docker”}}]}}}, {“insert”: {“rule”: {“family”: “ip”, “table”: “firewalld”, “chain”: “nat_PREROUTING_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “iifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “nat_PRE_docker”}}]}}}, {“insert”: {“rule”: {“family”: “ip6”, “table”: “firewalld”, “chain”: “nat_PREROUTING_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “iifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “nat_PRE_docker”}}]}}}, {“insert”: {“rule”: {“family”: “inet”, “table”: “firewalld”, “chain”: “mangle_PREROUTING_ZONES”, “expr”: [{“match”: {“left”: {“meta”: {“key”: “iifname”}}, “op”: “==”, “right”: “docker0”}}, {“goto”: {“target”: “mangle_PRE_docker”}}]}}}]}
Okt 23 11:12:50 box systemd[1]: docker.service: Main process exited, code=exited, status=1/FAILURE
Can somebody help?
Thanks
Mebus
Dennis Payne
For a UI, I’ve been using portainer which is recommended by lazydocker as an alternative. It is easier to convince my Windows using colleagues to use that over a terminal UI.
cirelli94
It would be nice to have this informations on https://fedoraproject.org/wiki/Docker#Installing_Docker !
Rajin Gill
After upgrading to Fedora 35 and reenabling cgroups – any docker run afterward would result in an OCI runtine cgroup error. After some investigation, I found that this problem does not occur on a clean installation of Fedora 35.
Turns out I was bit by this bug https://github.com/docker/for-linux/issues/1198 and had a rogue crun in /opt/containerd/bin. Removing it fixed the problem.
Hope this helps somebody.