Problem statement
Imagine you bought a new laptop with a shiny new USB-C docking station. You install fresh Fedora, encrypt your hard drive because laptop is a travel equipment and you do not want to travel around with non-ecrypted hard drive. You finish the installation, close the lid because you have external monitor, reboot the machine, and finally you would like to enter the LUKS password using the external keyboard attached using USB 2.0 to the USB-C docking station but it does not work!
The keyboard does not respond at all. So you open the lid, try the built-in keyboard which works just fine and once the machine boots the external keyboard works just fine as well. What is the problem?
What is this Thunderbolt anyway and why would anyone want it?
Thunderbolt is a hardware interface to connect peripherals such as monitors, external network cards [1] or even graphic cards [1]. The physical connector is the same as USB-C, but there is usually a label with a little lightning right next to the port to differentiate “plain” USB-C from Thunderbolt ports.

Of course it comes with very high transmission speed to support such demanding peripherals, but it also comes with a certain security risks. To achieve transmission speed like this, Thunderbolt uses Direct Memory Access (DMA) for the peripheral devices. As the name suggests, this method allows the external device to read and write memory directly without talking to the running operating system.
I guess you can already spot the problem here. If some stranger is walking around my laptop (even with the screen locked), is it really possible to just attach a device and read content of my computer memory? Let’s discuss it in more detail.
User facing solution for Thunderbolt security
In the recent versions, Gnome settings include a tab for Thunderbolt device configuration. You can enable and disable DMA access for external devices and you can also verify identity of the devices.
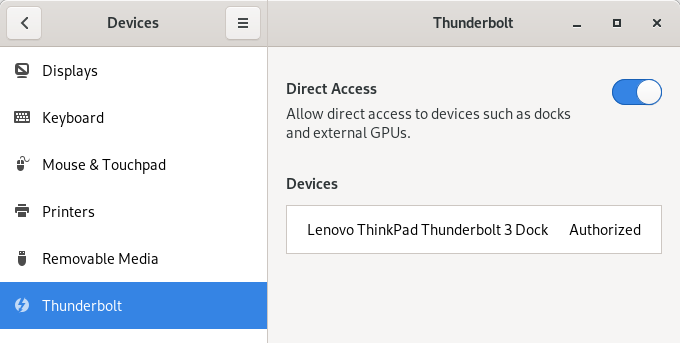
bolt is the component responsible for managing thunderbolt devices. See man 8 boltd for more information.
CLI tools
Of course it is possible to control the same via command line. I suggest you to read man boltctl or check the upstream repository directly: https://gitlab.freedesktop.org/bolt/bolt
Pre-boot support – solution to the keyboard problem
In pre-boot environment, the situation is slightly different. The userspace service responsible for device verification is not yet running so if a device is to be allowed, the firmware must to it. In order to enable this feature go to your BIOS and look for “support in pre boot environment”. For example this is how it looks on a Lenovo laptop:
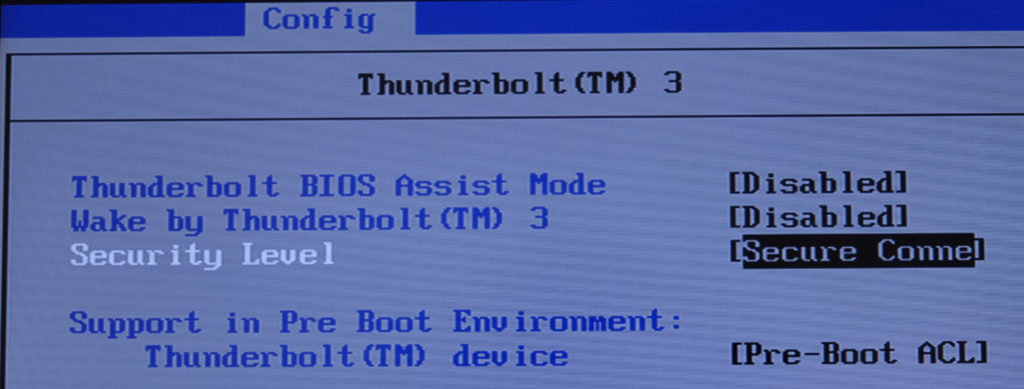
Once you enable this feature, bolt will add any verified device to a list of allowed devices. The next time you boot your machine, you should be able to use your external keyboard.
Run boltctl a look for “bootacl”. Make sure that the list of allowed devices contains the one you wish to use.
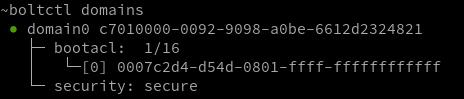
Also note the “security: secure” line. If you see anything else, for instance “security: user” I recommend to reconfigure BIOS.
Technical details of the pre-boot support
There is one unfortunate technical detail about this solution. Thunderbolt support different security levels. For running Fedora, I recommend you to use “secure” level to verify that the device is indeed the one that it claims to be by using a per-device key generated by the host and stored in the device. Firmware, on the other hand, will only use “user” level which uses simple UUID that is provided by the device. The difference is that a malicious device could claim to be a different one by providing the same UUID as a legitimate one. Anyway this should not be a problem as the memory does not contain any sensitive data yet.
You can find more technical details in this blog post: https://christian.kellner.me/2019/02/11/thunderbolt-preboot-access-control-list-support-in-bolt/
Conclusion
As you can see, in recent enough Fedora version the solution is a simple switch in BIOS. So if you are still opening your laptop during boot, go ahead and configure it so you don’t have to do it next time. Meanwhile check that the default security level is “secure” instead of “user” [5].
Sources:
[2] https://christian.kellner.me/2019/02/11/thunderbolt-preboot-access-control-list-support-in-bolt/
[3] https://gitlab.freedesktop.org/bolt/bolt
[4] https://wiki.gnome.org/Design/Whiteboards/ThunderboltAccess
[5] https://christian.kellner.me/2019/02/27/thunderclap-and-linux/






pr0PM
UEFI is more appropriate to be used there, BIOS is an outdated term and no longer exists.
Martin Sehnoutka
Thanks for your comment. Yes, UEFI is more technically correct, but it seems to me that it is common to use “BIOS” for “whatever is the first screen that appears after boot”.
Alex
I really like the casual – yet- accurate language here.