There are many stories about teaching open source in schools and universities. The teachers representing free and open source software come up with creative ways of teaching the lessons of open source to students. The Rochester Institute of Technology is one of these schools, offering a cross-disciplinary Free and Open Source Software minor to its students. One of the courses in this minor, Free and Open Source Culture, takes a step away from the programmatic side of things and looks more at the culture, ethics, and reasons for why working in the open is fundamental for software and communities.
In this class, students are tasked with a project to explain open source culture or ethics in a unique way. RIT student and former Magazine star Brendan Whitfield came up with an interesting and creative way to teach fellow classmates about the differences between open and proprietary software. Using the idea of a trust model, Whitfield designed a curious invention.
Presenting the black box
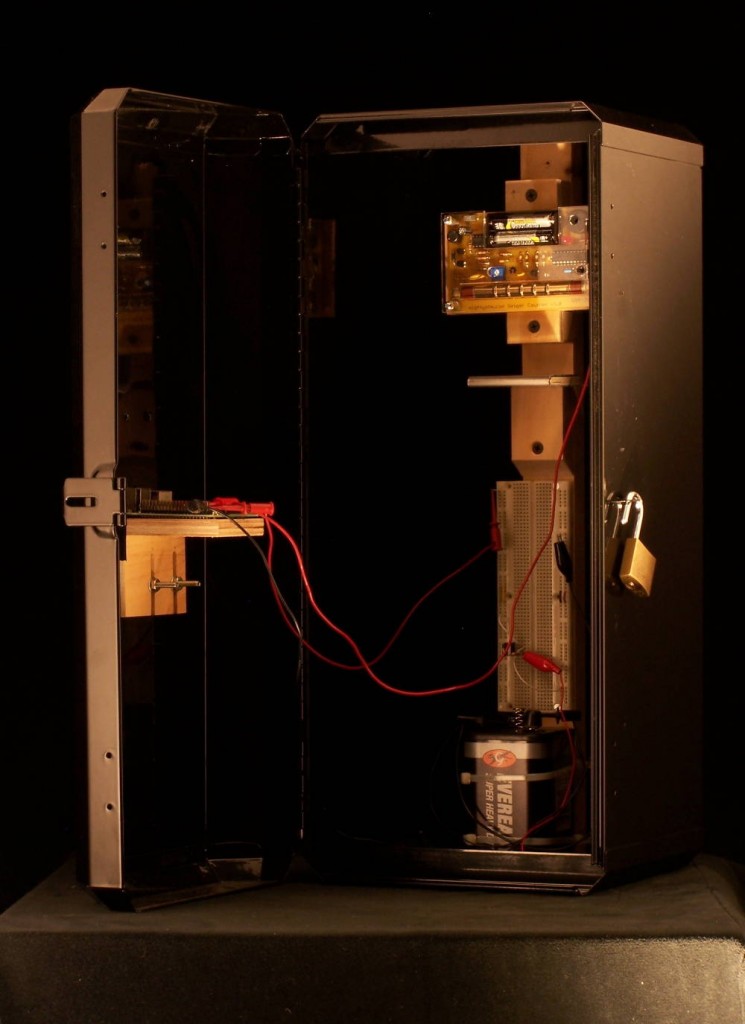
For the project, Whitfield opens the presentation by bringing a large, towering, black box into the classroom. It only has one Ethernet port on the front of it, and the door to open it is closed tightly with a lock. Other students have a chance to take in the creation and wonder… what is it? Whitfield is not one to disappoint, and gets to the point.
He begins explaining that the box offers a special, unique service that can not be found in other boxes of its kind. Anyone may connect their computers to the box via an Ethernet cable. Then, inside of a terminal app, they are able to use a homemade encryption service for encrypting communications, data, and more. Whitfield goes on to say how the output of the encryption is absolutely unbreakable and there are no downsides to using his encryption method. When asked how it works, he refuses to give specifics about the algorithm.
Encrypting behind closed doors
The invitation is extended to others in the room to try out the machine and to try encrypting their own secret messages with the black box. With a terminal open, curious volunteers enter a phrase in the terminal and are given an encrypted string of output in return. Whitfield then goes to show that when they run the box’s decryption method, it seamlessly translates it back to the original message.
Without any words about the box’s contents, Whitfield reaffirms that the box’s output is unbreakable. With a smile, he asks, “What could possibly be wrong about this?”
Breaking down the algorithm
After fielding eager questions to understand how the encryption method works and what is inside the box, Whitfield finally breaks. In a new terminal window, he runs a few commands that display a simple table, showing the original messages mapped to their encrypted counterparts. He begins explaining that the box doesn’t actually do any real encryption at all. It simply takes the string, generates random output from
, and maps the random phrase to the original message. The decryption command simply looks up the random phrase in the table and returns the original message it was paired with.
The lesson of open source slowly becomes more clear. Whitfield tells how in the mirage of being “unbreakable” as he so claimed, the truth is that nobody except the creator had any idea what was actually happening. By closing the source off from the community, there was no way to verify the soundness of the “encryption” or even what it was doing in the first place. By working in the open, there would have been no doubt that the implementation was outrageous.
But what’s inside the black box?
Yet one question is still unanswered. What is actually inside the black box? Whitfield reminds the listeners that the phony encryption is based on random numbers, and with that, the lock is popped off and the door slowly opens.
As the door opens, a frantic clicking sound begins coming out of the box. Inside, there is a Raspberry Pi fitted to a board with a Geiger counter attached. But what is attached to the Geiger counter? Simply a radioactive sample of Strontium-90! The random data being fed to the program was the output of the Geiger counter reading the radioactivity of the Strontium-90 sample. Little did the audience know this “closed source” tool was using radioactive samples to generate its cipher-text!
The faces of the audience fall to surprise, then shock, and finally laughter. Whitfield concludes his presentation showing that despite what a proprietary product promises, you can never be assured of what is really happening “under the hood”. His example took a literal application of the phrase!
Interviewing Whitfield
Fedora Magazine caught up with Whitfield and we had a chance to ask him a few questions about his creation.
FM: Introduce yourself. Tell us a bit about yourself.
“Hi, I’m Brendan Whitfield, and I’m from Rochester NY, USA. I am studying at Rochester Institute of Technology, where I’m majoring in New Media Interactive Development, and am minoring in Free and Open Source Software.”
FM: For building the Black Box, what was your motivation behind building this and what lesson did you want to teach?
“As part of a class in Free & Open Source Culture at RIT, the danger of black boxes was a recurring theme. A machine that can transact input and output without its internals ever being known is the poorest of shots at reassurance. So, for a final project, I decided to take this concept as literally as possible. I set out to make a physical black box that performs closed source encryption. Cryptography seemed to be an obvious choice, given that it is the source of much mayhem at the moment. Insecure cryptography can also be a hard thing to visualize, so to make it obvious, I picked a rather blunt insecurity.
The black box I constructed is advertised as a closed source symmetric-key encryption device that produces “unbreakable” cipher-text. Through a simple command line interface, users may submit text to be encrypted or decrypted, but the details of the encryption remain a mystery. With the intention of raising suspicion over closed source cryptography, I decided to make the internals of the box quite duplicitous. While my scheme of using lookup tables for the “encryption” was plenty devious, I figured I could add to the shock by taking this a step further. So, to generate the random cipher-text, I built a hardware random number generator using readings from a Geiger counter, and a sample of Strontium-90.”
FM: Why do you think teaching open versus proprietary in this way is important?
“You can never fully trust a closed source technology to be safe. In the words of Eben Moglen (regarding the Volkswagen fiasco, but still pertinent), “Proprietary software is an unsafe building material, you can’t inspect it.” Especially when a system is responsible for things that we value, such as privacy, this inability to inspect is cause for great suspicion. My black box is simply a physical representation of an extreme case.
People quickly understand that I’m faking the cryptography (that is, after all, the point), but I’m also counting on people to assume that there isn’t Strontium-90 in the box. I’m counting on them to assume that I’m a trustworthy person, and not a mad scientist wannabe. It’s that little extra shock of “I was not expecting that…” that this project is designed to induce. When it’s closed source, who knows, it might be radioactive.
The irony is, most of the technologies in the box are actually open source. I’m using a Raspberry Pi, a MightyOhm Geiger Counter, and some of my own open source software.”
FM: Is there anyone you have found most helpful in learning about open source in your classes and applying it in the real world?
“I’ll have to give this prize to Remy DeCausemaker, who has since moved on from being my professor to being a community lead for the Fedora Project.”
FM: What was the weirdest response you’ve seen or strangest question you’ve heard after presenting the Black Box to someone?
“I have yet to see anything truly weird. However, the look on people’s faces can be absolute gold. When I mention radiation, people simply chuckle in disbelief. But when they realize that you were serious, and they hear the Geiger counter clicking, they take a few steps back.
A common question I get: “Radiation?! Is that legal?”
The radioactive source that I am using is a tiny, license exempt quantity that anyone can legally own. They are typically used in schools for nuclear chemistry labs. It was shipped to my door.
I should mention that I do take radiation seriously. I chose Strontium-90 specifically because it is a beta emitter, and can be stopped with some simple aluminum shielding. Even unshielded, the majority of the radiation dissipates after ~4 inches of air space (obviously, I do not let anyone handle the source). As long as you don’t ingest it, you’re fine.”
FM: If you could take this project further, what would you do?
“Some of my notes for future iterations of the project:
- Have the box brick itself if a “non-authorized repair person” tries to open it.
- Install a long-term power source. Something to keep it going for a year or more (adds to the disbelief).
- Install a radiation warning light on the inside, but a broken one. The light bulb’s design is proprietary, and the guy who knows how to fix it already left the company.”
Don’t close your box!
We’d like to make a special thanks to Brendan for allowing us to interview him and show off his project. If you’re interested in learning more about the black box and Brendan’s other projects, you can read more on his website. You can also find the source code for the kernel module he wrote to handle the Geiger counter input on GitHub. Additionally, you can read Brendan’s earlier story about his open source laser interface software on the Fedora Magazine.







Kostic
Excellent article. Really enjoyed reading it!
Somewhat Reticent
Typical conflation of Open-Source (development protocol) with Freed-vs-Proprietary (licensing).
M. Saad
That’s a brilliant idea. I wonder if Brendan has ever considered presenting it at TED.